Security Model¶
Overview¶
The OVES Access Management system implements a comprehensive security model based on Zero Trust Architecture principles, ensuring that every user, device, and request is verified before granting access.
Security Principles¶
1. Zero Trust Architecture¶
Never Trust, Always Verify
- Verify identity for every user and device
- Grant least privilege access
- Monitor and log all activities
- Assume breach and limit blast radius
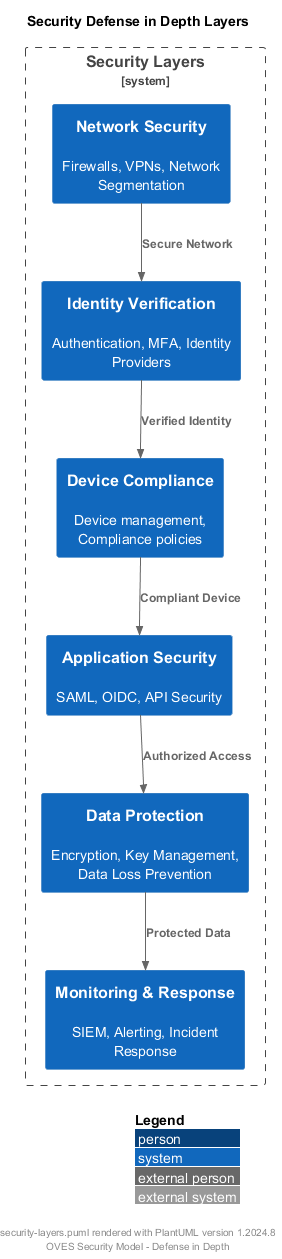
2. Defense in Depth¶
Multiple layers of security protection:
Click diagram to view PlantUML source
3. Principle of Least Privilege¶
- Users receive minimum necessary permissions
- Just-in-time access for administrative tasks
- Regular access reviews and cleanup
- Role-based access control (RBAC)
Identity Security¶
Azure AD Security Model¶
Multi-Factor Authentication (MFA)¶
- Required for all users without exception
- Multiple authentication methods supported
- Risk-based conditional access
- Hardware security key support for admins
Conditional Access Policies¶
| Policy | Condition | Action |
|---|---|---|
| High-Risk Sign-in | Risk level: High | Block access |
| Unmanaged Device | Non-compliant device | Require MFA + App Protection |
| Legacy Authentication | Old protocols | Block completely |
| Admin Access | Privileged roles | Require compliant device + MFA |
| Geographic | Outside approved regions | Require additional verification |
Privileged Identity Management (PIM)¶
PIM Configuration:
Just-in-Time Access:
- Temporary elevation (max 8 hours)
- Approval workflow required
- Multi-person approval for critical roles
Access Reviews:
- Quarterly for all privileged roles
- Monthly for Global Administrators
- Automatic removal of unused access
Monitoring:
- Real-time alerts for privilege escalation
- Detailed audit logs
- Risk scoring for admin activities
Keycloak Security Model¶
Customer Data Protection¶
GDPR Compliance - Data minimization principles - Explicit consent management - Right to be forgotten implementation - Data portability support
Privacy by Design - Pseudonymization of personal data - Encryption at rest and in transit - Regular data protection impact assessments - Privacy-preserving authentication flows
Session Security¶
{
"sessionSecurity": {
"settings": {
"idleTimeout": "30 minutes",
"maxSessionLength": "8 hours",
"rememberMeExpiry": "30 days",
"tokenLifetime": "1 hour",
"refreshTokenLifetime": "30 days"
},
"cookies": {
"sameSite": "Strict",
"secure": true,
"httpOnly": true,
"domain": ".oves.com"
},
"security": {
"bruteForceProtection": true,
"maxLoginFailures": 5,
"waitIncrementSeconds": 60,
"maxDeltaTime": "12 hours"
}
}
}
Application Security¶
Odoo Security Integration¶
Federated Authentication¶
- SAML 2.0 for Azure AD integration
- OpenID Connect for Keycloak integration
- Token validation and claims mapping
- Session federation and single logout
Role Mapping and Separation¶
Role Mapping:
Azure AD → Odoo:
"OVES-Employees": "Internal Users"
"OVES-Sales": "Sales Team"
"OVES-Contractors": "Limited Users"
"OVES-Admins": "System Administrators"
Keycloak → Odoo:
"Customer": "Portal Users"
"Partner": "Partner Users"
"Franchisee": "Franchise Users"
"VIP-Customer": "Premium Portal Users"
Data Separation:
Internal Data:
- Managed by Azure AD permissions
- Full business process access
- Internal reporting and analytics
External Data:
- Managed by Keycloak permissions
- Limited to customer-specific data
- Privacy-compliant data access
Secret Management¶
Azure Key Vault Integration¶
Secret Categories¶
| Secret Type | Storage Location | Access Method | Rotation Policy |
|---|---|---|---|
| Database Connections | Azure Key Vault | Managed Identity | 180 days |
| API Keys | Azure Key Vault | Service Principal | 90 days |
| Certificates | Azure Key Vault | Automated renewal | Before expiry |
| Encryption Keys | Azure Key Vault HSM | Hardware security | 1 year |
Access Policies¶
# Example Key Vault access policy
Set-AzKeyVaultAccessPolicy `
-VaultName "OVES-Secrets-Vault" `
-ObjectId $groupObjectId `
-PermissionsToSecrets @("Get", "List") `
-PermissionsToKeys @("Get", "List", "Decrypt", "Encrypt") `
-PermissionsToCertificates @("Get", "List")
Keycloak Secret Management¶
Client Secrets¶
- Automatic rotation for service accounts
- Secure client credential flows
- Token introspection for validation
- Revocation capabilities
External Identity Provider Secrets¶
- Encrypted storage of OAuth client secrets
- Secure callback URL validation
- Token exchange security
- Regular credential auditing
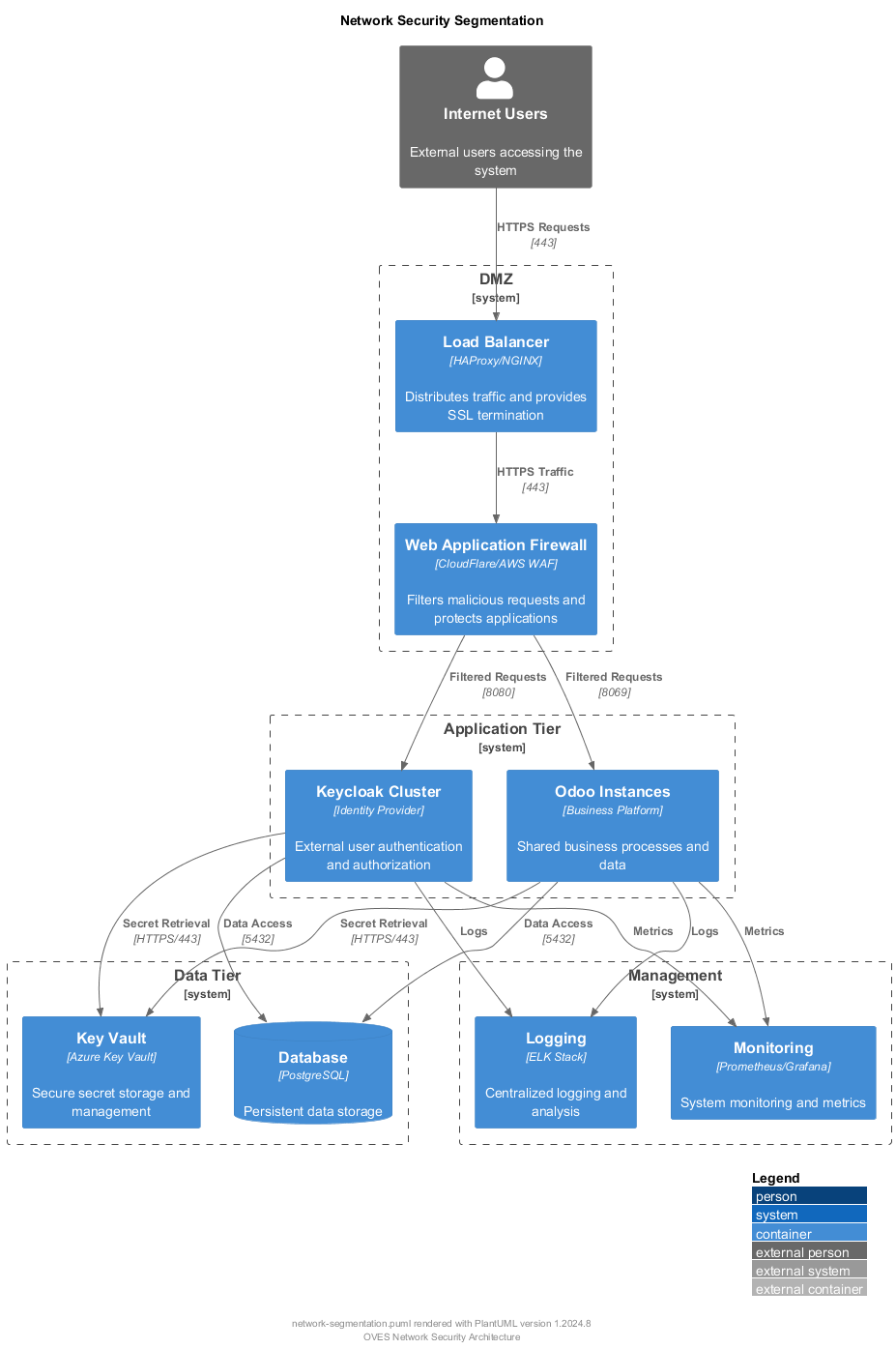
Network Security¶
Network Segmentation¶
Click diagram to view PlantUML source
Security Groups and Firewall Rules¶
| Source | Destination | Port | Protocol | Purpose |
|---|---|---|---|---|
| Internet | Load Balancer | 443 | HTTPS | Public access |
| WAF | Keycloak | 8080 | HTTP | Internal communication |
| WAF | Odoo | 8069 | HTTP | Internal communication |
| App Tier | Database | 5432 | PostgreSQL | Database access |
| App Tier | Key Vault | 443 | HTTPS | Secret retrieval |
Monitoring and Detection¶
Security Information and Event Management (SIEM)¶
Log Sources¶
- Azure AD: Sign-in logs, audit logs, risk detections
- Keycloak: Authentication events, admin actions
- Odoo: Business process logs, data access
- Infrastructure: System logs, network traffic
Alert Rules¶
{
"alertRules": [
{
"name": "Suspicious Login Activity",
"condition": "Multiple failed logins from same IP",
"threshold": 5,
"timeframe": "5 minutes",
"severity": "High",
"action": "Block IP and notify security team"
},
{
"name": "Privilege Escalation",
"condition": "Role assignment changes",
"threshold": 1,
"timeframe": "Immediate",
"severity": "Critical",
"action": "Immediate notification and review"
},
{
"name": "Unusual Data Access",
"condition": "Access to sensitive data outside normal hours",
"threshold": 1,
"timeframe": "1 hour",
"severity": "Medium",
"action": "Log and review"
}
]
}
Threat Detection¶
Behavioral Analytics¶
- Machine learning-based anomaly detection
- User and entity behavior analytics (UEBA)
- Risk scoring for authentication events
- Automatic response to high-risk activities
Indicators of Compromise (IoC)¶
- Known malicious IP addresses
- Suspicious user agent strings
- Impossible travel scenarios
- Credential stuffing patterns
Incident Response¶
Security Incident Classification¶
| Severity | Description | Response Time | Escalation |
|---|---|---|---|
| Critical | Active data breach, system compromise | 15 minutes | CISO, Legal |
| High | Unauthorized access, privilege escalation | 1 hour | Security team |
| Medium | Policy violations, suspicious activity | 4 hours | IT team |
| Low | Information gathering, reconnaissance | 24 hours | Monitoring team |
Response Procedures¶
- Detection and Analysis
- Automated alert triggered
- Initial triage and validation
- Impact assessment
-
Evidence preservation
-
Containment
- Immediate threat isolation
- Account lockdown if necessary
- Network segmentation
-
System isolation
-
Eradication and Recovery
- Root cause analysis
- System hardening
- Credential rotation
-
Service restoration
-
Post-Incident Review
- Lessons learned documentation
- Process improvements
- Policy updates
- Training updates
Compliance and Auditing¶
Compliance Frameworks¶
- SOC 2 Type II: Security, availability, processing integrity
- GDPR: Data protection and privacy
- ISO 27001: Information security management
- NIST Cybersecurity Framework: Identify, protect, detect, respond, recover
Audit Requirements¶
Regular Audits¶
- Monthly: Access reviews and cleanup
- Quarterly: Security policy compliance
- Annually: Penetration testing and vulnerability assessment
- Continuously: Automated compliance monitoring
Audit Trail Requirements¶
- Immutable logging for all authentication events
- Data retention for minimum 7 years
- Log integrity verification
- Compliance reporting automation
Security Metrics and KPIs¶
Key Performance Indicators¶
| Metric | Target | Measurement |
|---|---|---|
| MFA Adoption | 100% | Users with MFA enabled |
| Patch Compliance | >95% | Systems with latest security patches |
| Incident Response Time | <15 min (Critical) | Time to initial response |
| Failed Login Rate | <5% | Ratio of failed to successful logins |
| Access Review Completion | 100% | Completed reviews within SLA |
Risk Metrics¶
- Identity Risk Score: Calculated based on user behavior
- System Vulnerability Score: Based on security assessments
- Compliance Score: Percentage of controls implemented
- Threat Detection Accuracy: True positive rate for alerts
Next: Implement these security controls using our Implementation Guides or explore Best Practices.